Starting November 10, 2025, the Department of Defense will begin a phased rollout of CMMC 2.0 requirements in new solicitations. Show up without the right certificate, and contracting officers won’t even open your bid. That shift turns 2026 into the year CMMC 2.0 compliance tools change from nice-to-have to must-have.
Spreadsheets struggle to effectively track and manage the 110 security controls required by NIST SP 800-171 Revision 2, especially when considering the hundreds of associated assessment objectives. Modern platforms pull evidence from AWS, Azure AD, and every laptop, compressing months of prep into hours of API calls.
In this guide, you’ll learn how to pick the right CMMC 2.0 compliance tool—what to demand, what to skip, and how to stay audit-ready while chasing new contracts.
The state of CMMC 2.0 in 2026
Enforcement timeline
The Department of Defense published the final rule amending the Defense Federal Acquisition Regulation Supplement (DFARS) to include CMMC requirements on September 10, 2025. This followed the publication of the main CMMC Program Rule (32 CFR) on October 15, 2024. Under federal rule-making timelines, it became enforceable 60 days later on November 10, 2025. From that date forward, contracting officers have added a CMMC clause to every new solicitation.
- Level 1 self-assessment for work that handles only Federal Contract Information (FCI)
- Level 2 requirements: self-assessment for routine Controlled Unclassified Information (CUI), plus a third-party Level 2 certification for high-priority programs
No grace period exists. Proposals that arrive without the correct certificate are tagged “non-responsive” and discarded.
DoD is rolling the mandate out in three phases that run through 2028. Phase 1 applies to new contract awards, Phase 2 covers option-year modifications and recompetes, and Phase 3 extends the requirement to lower-tier subcontractors. The schedule gives large primes time to coach suppliers, yet many small and midsize businesses have barely a year to finish a Level 2 audit—a process that often takes nine months from kickoff to sign-off.
Bottom line: 2026 is the fork in the road. Treat CMMC as a side project now, and next year’s pipeline could vanish.
The hidden cost of manual compliance
Picture a typical gap-analysis sprint: someone copies a spreadsheet, engineers drop in screenshots, HR emails training logs, and a project manager stitches everything together before the assessor shows up. Each data pull interrupts real work, and every screenshot can be stale within minutes.
Multiply that churn across all 110 NIST 800-171 practices and you can burn 200 to 300 staff-hours per audit cycle. Time that large could fund feature work instead of paperwork.
Manual tracking hides a tougher penalty: unseen gaps. Spreadsheets never warn you when multifactor authentication is disabled or a critical patch slips. When an assessor finally spots the lapse, you face a corrective-action plan and a delayed contract start. Automation platforms pull live configuration data, flag drift in real time, and surface every issue on a single dashboard.
Driving toward CMMC with spreadsheets is like crossing the country on paper maps while competitors navigate with GPS. Detours stack up, fuel costs climb, and when you arrive, the deal is gone.
Key evaluation criteria for CMMC tools
Depth of automation and integrations
The difference between a half-automated tool and a true compliance platform usually comes down to integrations. According to Vanta’s 2024 State of Trust Report, organizations are spending an average of 11 working weeks per year on compliance tasks, an increase from the previous year, underscoring the growing burden of manual evidence collection. That finding underscores a simple truth: automation works only when the platform can see your entire stack.
Look for direct, read-only APIs into cloud providers, identity stores, endpoint agents, and ticketing queues. A mature platform such as Vanta’s CMMC compliance software connects with more than 400 systems, pulling configuration data continuously so screenshots and email attachments disappear from the audit prep cycle. More integrations translate into fewer interruptions, faster remediation, and ultimately, smoother audits.
Coverage of CMMC levels, plus every other framework
Level 2, which covers all 110 NIST 800-171 practices, blocks or clears most contracts, so confirm that the tool tests every practice. Ask whether it already maps the 24 enhanced controls in NIST 800-172; that groundwork avoids a platform swap if Level 3 emerges in 2027. Built-in cross-mapping to SOC 2, ISO 27001, and FedRAMP lets a single MFA check satisfy multiple frameworks and keeps the executive dashboard consistent.
Real-time monitoring and alerts
Compliance drifts the instant someone spins up an unencrypted S3 bucket. Choose software that polls key systems every few minutes, flags failures, and opens a Jira or ServiceNow ticket automatically. A timestamped “found → fixed” trail impresses assessors more than a flawless snapshot.
Policy and documentation support
Auditors still expect a System Security Plan, policies for every control family, and a living POA&M. Platforms with template libraries allow you to answer context questions once, then generate boilerplate, version history, and gap tracking automatically. Documentation shifts from project to by-product.
Evidence management and the auditor portal
Robust tools tag every artifact—log, config, policy—to its control and store it immutably. During the audit, invite your C3PAO into a read-only portal where they can review evidence and leave inline questions. Customers of Vanta report cutting fieldwork from weeks to days with this approach.
Integration fit and ease of use
Native connectors beat Zapier workarounds. Confirm that the vendor provides an open API for niche systems, Intune hooks for device health, and Slack or Teams notifications. Role-based views let engineers drill into failing controls, while executives skim a heat-map summary. If the UI feels like a cockpit, adoption can stall; if it feels like Gmail, teams stay engaged.
Vendor expertise and support
Ask who authors the control mappings—former DoD assessors or generalist engineers. Check for in-house compliance advisors, 24×7 chat, and a named customer success manager. An assessor who already knows the portal can shave days off the audit.
Scalability and future frameworks
Performance must remain snappy when asset counts double after an acquisition. Multi-entity rollups, flexible licensing, and long-term data retention are table stakes. Also ask how quickly the vendor ships new frameworks; top platforms added NIST 800-171 Rev 3 controls within 30 days of release.
Total cost of ownership
Price the whole picture: integration limits, auditor seats, support tiers, and any per-asset fees. Offset that cost by estimating labor hours saved and potential early contract wins. A higher subscription often beats a bargain license that forces months of manual work.
Leading CMMC platforms at a glance
Vanta: automation breadth with cross-framework DNA
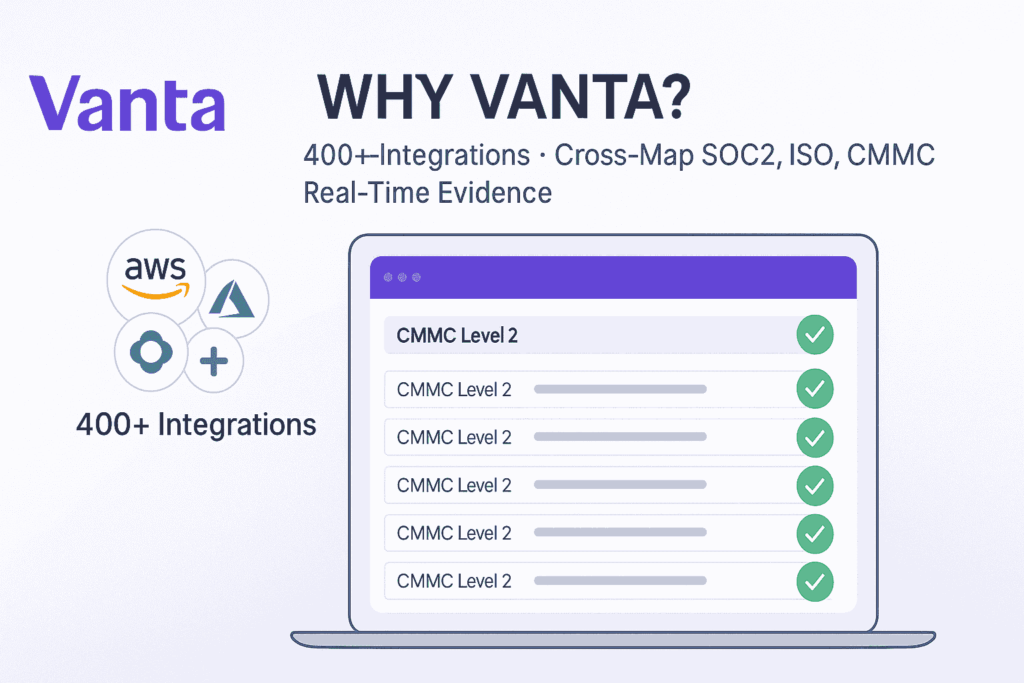
Vanta built its reputation on speeding up SOC 2 and similar audits; the same engine now supports CMMC with 400+ integrations and 1,200+ automated tests that monitor controls hourly. Their CMMC compliance software maps to the 110 Level 2 practices (NIST SP 800-171), with pre-built templates and guidance to streamline prep.
Each control is cross-mapped, so one MFA check satisfies SOC 2, ISO 27001, and CMMC at the same time. Executives view a single trust portal instead of juggling three slide decks.
Auditors benefit, too. A read-only Controlled Audit View lets C3PAOs review evidence, leave inline questions, and export reports without endless ZIP files. Customers report saving about a week of fieldwork when assessors use the portal.
Ideal fit: fast-growing tech companies or midsize suppliers chasing multiple certificates on tight timelines. Consideration: Vanta is API-first, so air-gapped or on-prem systems still call for manual uploads.
Scrut Automation: risk-first lens with broad framework support
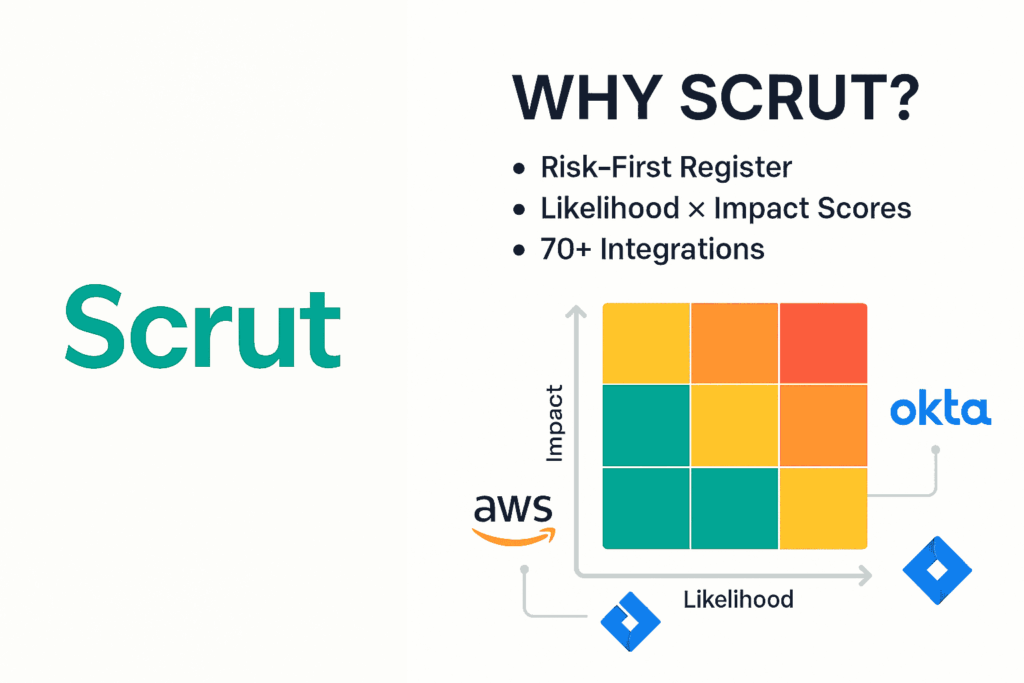
Scrut approaches CMMC through a risk register rather than a raw checklist. Every automated finding rolls into a likelihood-and-impact score, so executives see why a missing log-retention setting matters to revenue.
The platform offers more than 70 pre-built integrations with AWS, Okta, CrowdStrike, Jira, and more, capturing evidence automatically and updating scores in real time. You can also create custom controls, link them to internal policies, and track remediation in the same view. That flexibility pays off when a customer requests proof of a niche standard or when new CMMC guidance arrives mid-cycle.
Auditors receive a dedicated workspace that pairs each artifact with its risk context; seeing both evidence and quantified score shortens debate and keeps the assessment moving.
Ideal fit: teams that merge compliance with enterprise risk management and value room to model bespoke controls. Consideration: the richer interface carries a learning curve, so plan for a guided onboarding to smooth adoption.
Hyperproof: workflow flexibility for complex organizations

Hyperproof treats every CMMC practice as an assignable work item. Tasks live on Kanban-style cards where you can comment, attach artifacts, and link Jira or ServiceNow tickets, so compliance rides the same rails as Agile or ITSM.
Customization is the star. Build custom control sets, map them to corporate risk registers, and reuse evidence across 118 supported frameworks and more than 70 native integrations. Multi-entity rollups let large companies track ownership by business unit, avoiding duplicate work when SOX, PCI, and CMMC overlap.
Stakeholder reporting scales from log-level drilldowns to executive heat maps, cutting “data reconciliation” meetings.
Ideal fit: mid-market to enterprise organizations that plan to weave CMMC into a broader GRC program. Consideration: depth of configuration suggests assigning a dedicated admin or consulting partner; include that ramp in your timeline.
AuditBoard: enterprise audit alignment with CMMC overlay
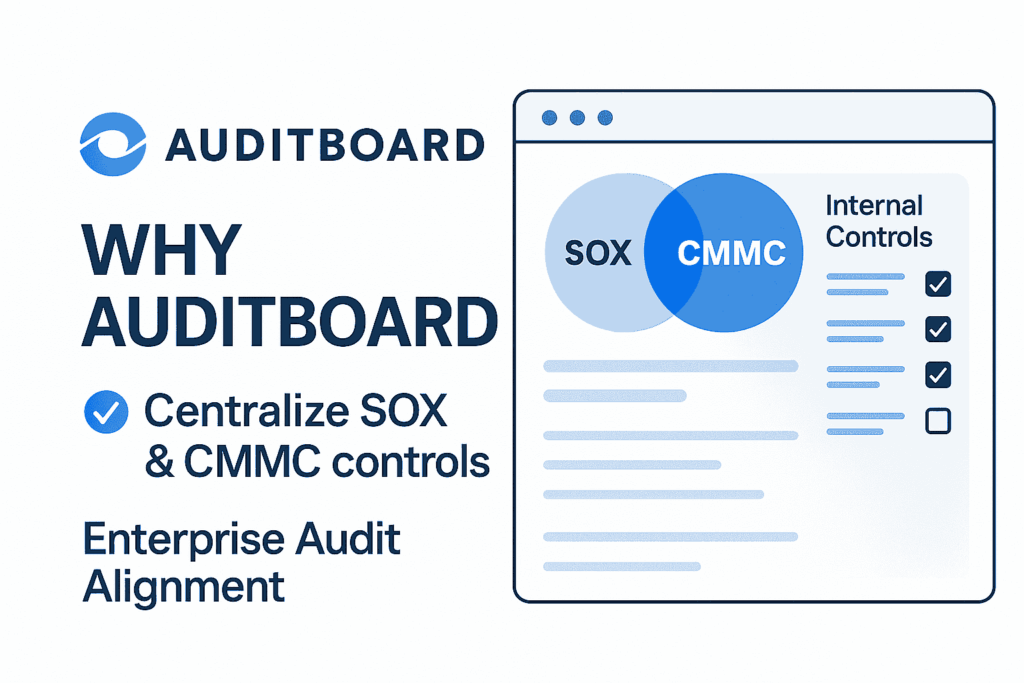
Originally built for SOX and financial audits, AuditBoard has expanded into CMMC by layering compliance frameworks over its internal controls platform. Its strength lies in centralizing testing, evidence, and auditor communication into a single system tailored to regulated enterprises.
Teams can map NIST 800-171 controls, assign ownership, and integrate with existing audit calendars and workflows. Risk modules and workflow automation make it ideal for companies that want CMMC compliance to live alongside broader internal audit operations.
Ideal fit: large primes or federal contractors managing multiple regulatory frameworks through internal audit. Consideration: may be overkill for smaller suppliers without an established audit team.
Exostar: supply chain pedigree with DoD-native workflows
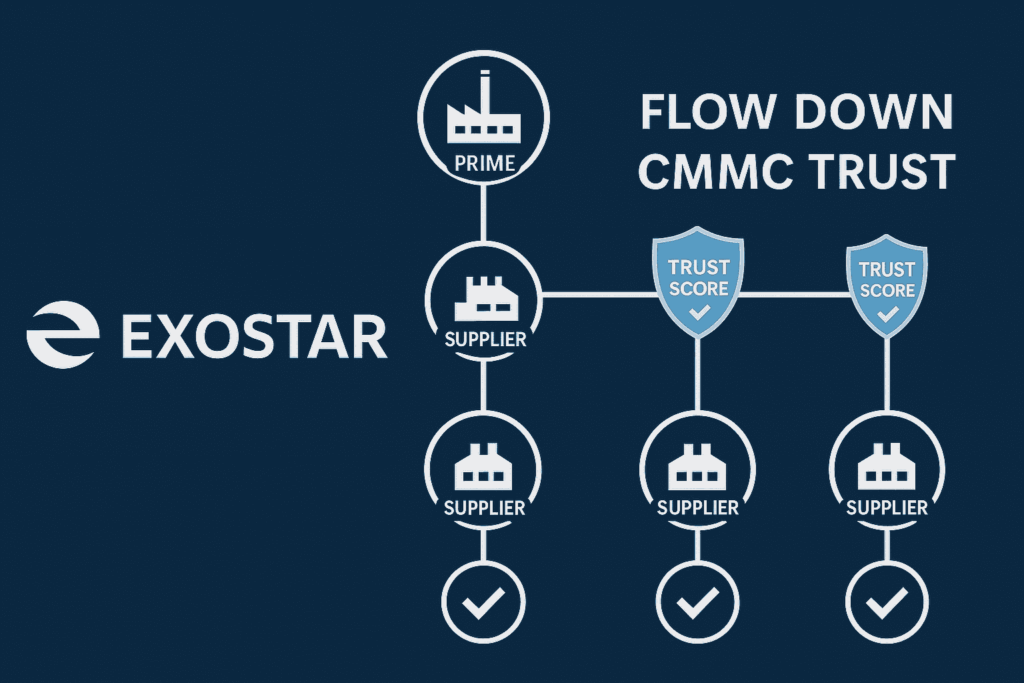 Exostar’s Partner Information Manager (PIM) suite is purpose-built for the defense industrial base. It offers CMMC-focused assessments, pre-populated NIST 800-171 control sets, and integration with eMASS workflows—the system the DoD uses to track cyber compliance.
Exostar’s Partner Information Manager (PIM) suite is purpose-built for the defense industrial base. It offers CMMC-focused assessments, pre-populated NIST 800-171 control sets, and integration with eMASS workflows—the system the DoD uses to track cyber compliance.
Exostar also helps prime contractors manage flow-down requirements and verify that lower-tier suppliers are CMMC-ready. Features like contractor onboarding, attestation workflows, and trust scoring make it unique among tools on this list.
Ideal fit: prime contractors and aerospace/defense firms managing subcontractor ecosystems.
Consideration: steep learning curve and pricing complexity make it a better fit for mature compliance teams.
RegScale: continuous compliance engine with engineering depth
RegScale takes a developer-first approach to compliance. The platform runs as a “compliance-as-code” engine, ingesting infrastructure metadata and configuration management files to create a real-time compliance state that engineers can query, test, and remediate via APIs.
It supports NIST 800-171, CMMC, and dozens of related frameworks, with features like versioned POA&Ms, control library mapping, and dynamic dashboards. For companies with DevSecOps pipelines, RegScale provides a near-instant view of compliance health as code and config change.
Ideal fit: tech-forward defense suppliers with internal engineering resources and a desire for infrastructure-as-code integration. Consideration: less visual guidance and fewer policy templates than traditional GRC tools—may require internal DevOps expertise.
How to choose the right platform
1. Define your scope and goals
List every contract in your pipeline and note the required CMMC level. A Level 1 self-attestation for marketing collateral is not the same project as a Level 2 third-party audit for CUI. Plot each deadline on a simple timeline: kickoff, gap analysis, remediation, readiness review, and audit. This exercise shows whether you need a quick-start tool or a multi-year GRC suite.
Gauge current maturity next. If you already hold SOC 2 or ISO 27001, a cross-mapping platform can reuse that work. If you are starting from scratch, look for guided policy templates and in-house advisor support. Finally, agree on success metrics early, such as “pass the audit by Q4” or “reduce compliance hours by 40 percent.” Clear targets keep vendor demos honest.
2. Identify must-have features
Translate pain points into requirements. Screenshots slowing audits? Put continuous evidence collection at the top of the list. GovCloud tenants? Prioritize deep integrations over AI summaries. Build a scorecard—automation depth, integration count, policy templates, auditor portal, support model—and assign a value to each column. Invite frontline users now; their must-haves can become blockers if discovered after purchase.
3. Shortlist three to five vendors
Use analyst reports, peer Slack channels, GRC tools list, and LinkedIn case studies to find tools that already produced Level 2 certificates. Include one automation-heavy platform, one enterprise GRC suite, and one SMB-friendly option so trade-offs stay visible. Share your scorecard with each vendor and request written replies before scheduling demos.
4. Take advantage of demos and trials
Ask every vendor to walk through a real control, for example, “ensure all admin accounts use MFA.” Time how long it takes to detect the setting, pull evidence, and flag drift. If a sandbox is available, load dummy data and explore without a sales engineer nearby. Keep your scorecard open and grade in real time.
5. Evaluate implementation effort
Confirm hours, not weeks, to wire integrations, import assets, and configure roles. Ask who does the work: a named implementation engineer or your already busy sysadmin. Request a sample project plan that lists each milestone and responsible party.
6. Consider partner and assessor input
Loop your C3PAO or RPO into the process early. An assessor who knows your chosen portal can save days of fieldwork and may discount the engagement. If you have not selected a C3PAO, software familiarity can break the tie.
7. Pilot and iterate
Activate one cloud account or control family first. Meet weekly to review alert noise, evidence timestamps, and ticket closure. Document every hiccup so the wider rollout starts clean. Expand in waves, reusing scripts and lessons learned.
8. Measure success criteria
Track hours per month on evidence collection, open control failures, and mean time to remediation, aligning each metric with broader cybersecurity best practices. Compare those numbers with your pre-platform baseline so leadership sees the return on investment. Revisit metrics quarterly; adjust alert thresholds, retire unused reports, and double down on dashboards that drive decisions. Continuous monitoring should feel like a heartbeat, not a fire drill.
Conclusion and next steps
CMMC 2.0 stopped being “future work” on November 10, 2025, the day new DoD contracts began requiring certification. From that point forward, an up-to-date certificate serves as a gate, not a nice-to-have.
The upside: automation platforms turn compliance from a last-minute scramble into a daily rhythm. Evidence updates automatically, controls stay green, and formal audits shrink from marathons to sprints.
Next steps:
- Shortlist three vendors today.
- Book demos this week with the scorecard you created earlier.
- Pilot one business unit next month and track hours saved along with control drift caught.
Equip your team with technology that secures every 2026 bid with a valid certificate and the confidence to keep it current.
FAQs
What is the difference between CMMC Level 1 and Level 2 in 2026?
Level 1 requires a self-assessment for handling Federal Contract Information (FCI), while Level 2 mandates either a self-assessment or a third-party certification for Controlled Unclassified Information (CUI), depending on the contract’s criticality.
How long does CMMC Level 2 certification take in 2026?
From project kickoff to final certification, Level 2 typically takes 6–12 months, factoring in gap remediation, assessor availability, and evidence collection timelines.
Can CMMC compliance tools generate a System Security Plan (SSP)?
Most platforms provide templates and assist with SSP content, but final ownership rests with your organization or consulting partner. Always validate completeness before the audit.
What’s the biggest advantage of using a CMMC automation tool?
Automation tools reduce manual effort, flag compliance drift in real time, and streamline auditor collaboration—cutting prep time from months to weeks and increasing audit success rates.

